Connect with me on LinkedIn
Capstone Project - Offensive Cybersecurity
Summary
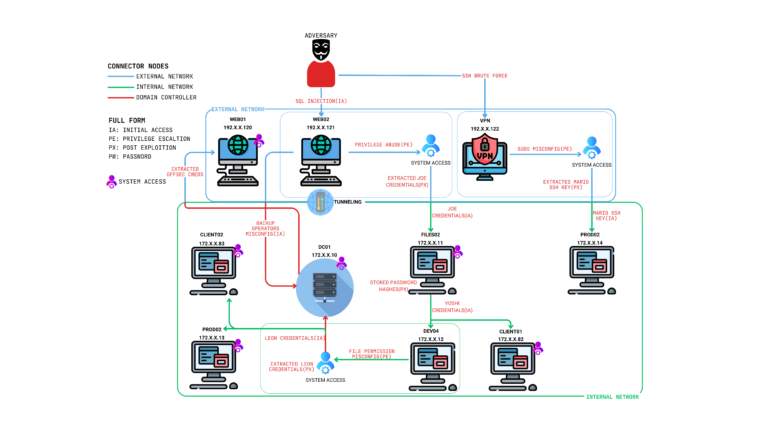
The penetration test was conducted on the Medtech environment to assess the security posture of its internal and external network infrastructure, identify vulnerabilities, and evaluate the risks associated with potential exploitation. The assessment aimed to simulate real-world attack scenarios to determine whether an unauthorized adversary could compromise the organization’s critical assets, including the Domain Controller (DC), and gain access to sensitive data.
This comprehensive evaluation encompassed a range of techniques, including network enumeration, vulnerability exploitation, privilege escalation, credential harvesting, and lateral movement. As discussed, this engagement was conducted using a black-box methodology, simulating an external attacker’s perspective with no prior knowledge of the environment to identify vulnerabilities and assess the organization’s security posture. The findings highlighted significant security gaps, such as improper configurations, weak access controls, and insecure credential storage practices. These vulnerabilities enabled an adversary to establish footholds on multiple machines, pivot between networks, and compromise the Domain Controller, ultimately exposing the organization to the risk of full domain compromise.
Results
The assessment revealed critical vulnerabilities across the Medtech environment that pose significant risks to the confidentiality, integrity, and availability of its systems and data. Key findings include:
- Domain Compromise: A misconfiguration in the Backup Operators group on the Domain Controller allowed unauthorized access to registry hives and NTLM hashes, enabling full domain compromise.
- Privilege Escalation: Several systems exhibited improper file permissions, insecure sudo configurations, and credential caching in memory, allowing attackers to escalate privileges to SYSTEM or root levels.
- Lateral Movement: Credential reuse across multiple systems and weak network segmentation enabled seamless lateral movement, exposing internal resources and critical infrastructure to exploitation.
- Sensitive Data Exposure: Poor handling of sensitive information, including plaintext credentials stored in log files and on administrative desktops, facilitated unauthorized access to key systems.
- Initial Access Vulnerabilities: Weak password policies and exploitable entry points, such as SQL injection in web applications and SSH services with low-complexity credentials, allowed attackers to gain footholds in the environment.
These vulnerabilities demonstrate systemic issues in security controls, leading to a cascading compromise of the Medtech network, including its most sensitive assets, such as the Domain Controller. Immediate remediation is critical to prevent further exploitation and secure the organization’s infrastructure
Interested? Let’s Chat.
Got an opportunity, idea, or just want to connect?
I’m always open to collaborations and conversations – feel free to reach out.